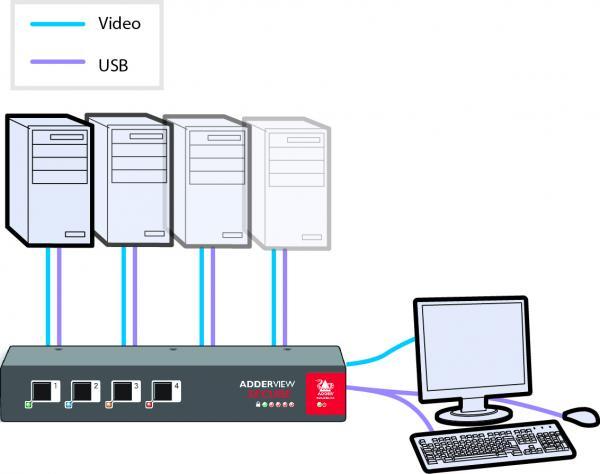
Adder AVSV1002 2 port EAL4+, EAL2+ Accredited & TEMPEST USB and VGA Secure KVM switch Independantly tested against common criteria and achieves Evaluation Assurance Level 4+. CERTIFICATION REPORT No. CRP259. It is hardwired so that data Diodes, implemented within hard-wired electronic circuitry, rather than software, are liberally employed to ensure that critical data paths can flow only in one direction. These data diodes ensure that a compromised peripheral, a keyboard for instance, cannot read information back from a connected system in order to transfer such details to another system. Whenever a channel is changed, the connected.
The AVSV1002 is part of AdderView Secure range of products that are highly robust KVM switches for critical applications. When information absolutely must not be leaked between systems or networks, the ADDERView AVSV1002 Secure KVM switch combines the necessary isolation with a desirable ease of use.
ADDERView AVSV1002 Secure unit combines a number of overlapping strategies that are designed to defeat potential points of infiltration or protect against user error.
The outer casing in the AdderView AVSV1002 contains extensive shielding to considerably reduce electromagnetic emissions. Additionally, the casing has been designed with as few apertures as possible to reduce the possibility of external probing and several primary chassis screws are concealed by tamper-evident seals to indicate any unauthorized internal access. Shielding extends also to the internal circuitry with strong levels of electrical crosstalk isolation between ports to protect against signals from one computer becoming detectable on another.